Stewart Hillhouse
Contributor
Stewart Hillhouse writes actionable growth marketing insights as senior content lead at
Demand Curve. By night, he interviews marketers and creatives on his podcast,
Top Of Mind. Before getting into marketing, Stewart was a semi-professional lumberjack. He also writes at
stewarthillhouse.com.
More posts by this contributor
There are very few marketing channels as well rounded as email newsletters. They provide a direct, owned line of communication with your audience; nearly 40x return on investment (~$40 generated per every dollar spent), are infinitely scalable and virtually free.
But to unlock these benefits, you’re going to need to be strategic. In this article, I’m going to share tactics we’ve used at Demand Curve to grow our newsletter list to over 50,000 highly-qualified subscribers and maintain an open rate of over 50%.
Increase popup conversion using the 60% rule
While they’re often thought of as intrusive, pop-ups work. On average, they convert 3% of site visitors, and strategic, high-performing pop-ups can reach conversion of about 10%.
To make higher-converting, less intrusive pop-ups, try the 60% rule.
- Choose a page you’d like to put a pop-up on. We recommend pages that aren’t conversion-focused (like product pages, checkout and sign-ups). We’ve found content pages work the best and they can act as a signal for visitors who are looking for something specific.
- Open your website’s analytics and see what the average time spent on that page is.
- Set your pop-up to appear after 60% of the average time of that page has elapsed.
So if the average time spent on a page is 50 seconds, set your pop-up to appear 30 seconds (60% of total time) after visitors land on that page.
Why 60%? Readers have shown interest in your content, but are nearing the end of their session. Prompting them to join your newsletter to see more relevant content in exchange for their email will feel fair.
To encourage new subscribers to open your welcome email, try breaking the welcome email pattern using delayed gratification and a recognizable sender.
Give samples of your newsletter to prove quality
If a visitor is new to your content, asking them to sign up for your newsletter can be a big step, and most new visitors won’t convert. To narrow the gap between a new reader and subscriber, provide a sample on the sign-up page. Use your most engaging newsletter as a sample to prove that your content is high quality.
To source your most engaging content, filter by open rate and replies. In your email service provider, sort your previous editions by open rate. This will help you identify which subject lines are most popular with existing readers. Modify your most popular subject line to turn it into a header on your newsletter sign-up page.
Next, go into your inbox and sort by replies to your newsletter. Identify which newsletter got the most replies from your readers. This is a positive signal that the content from that edition resonated the most and would be a solid choice for your free sample.
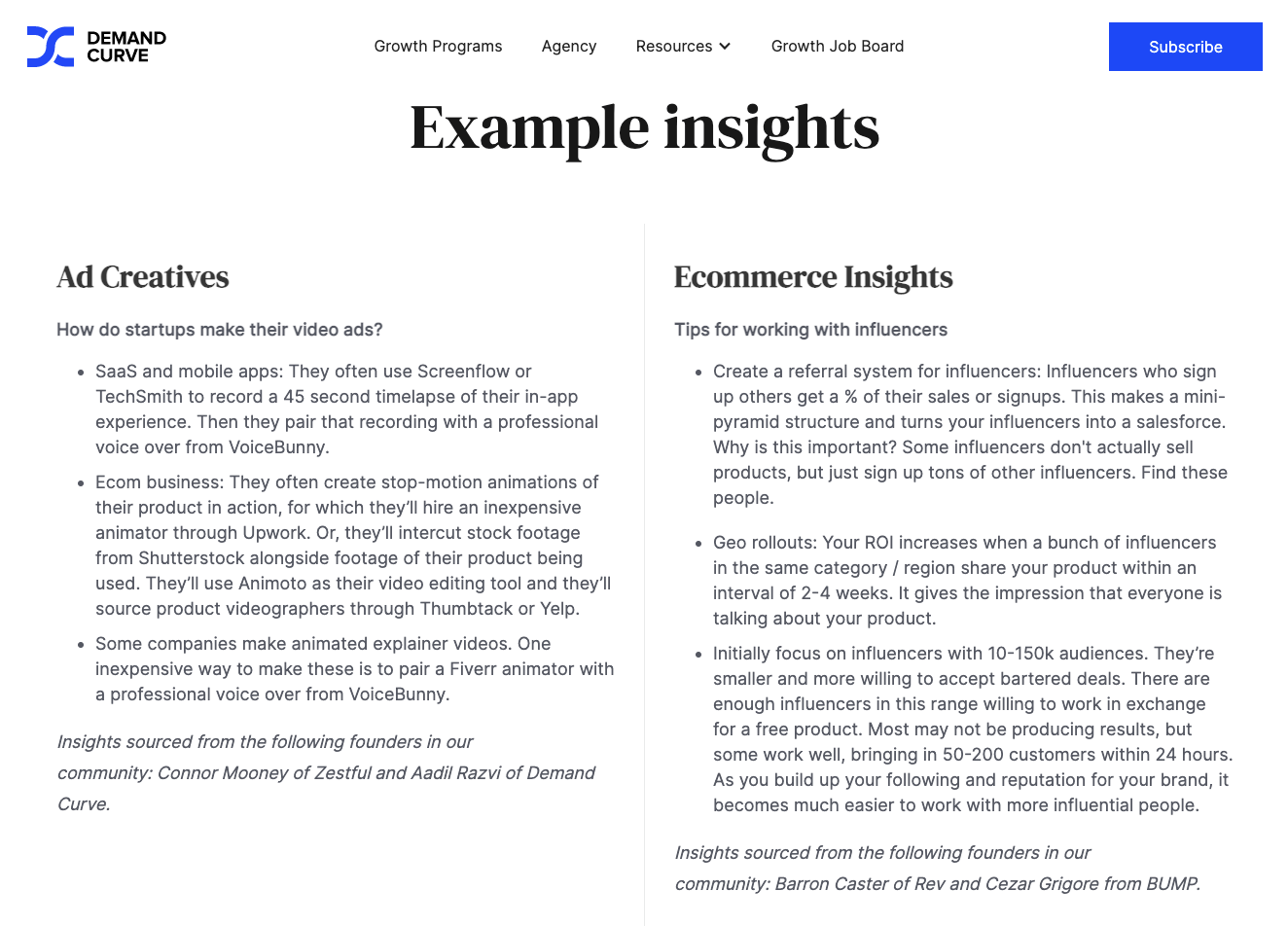
Image Credits: Demand Curve
Emails from real people are opened more often
People reflexively ignore welcome emails after they sign up. But, those who do open your welcome email are more likely to consistently open your newsletters.
To encourage new subscribers to open your welcome email, try breaking the welcome email pattern using delayed gratification and a recognizable sender.
Delay your welcome email by 45 minutes. This will bypass the reflex that new subscribers have to ignore an email that pings them seconds after signing up. We’ve found 45 minutes to be ideal, because the delay is long enough that it breaks the pattern, but not so long that your email gets buried in their inbox.
Send your welcome from a person, not from a business account. We’ve found this tactic to be especially effective when the sender is the founder of the business or someone with an established audience. Use a photo of that person and not your company logo to help the email stand out.
To avoid overflowing the sender’s real inbox, create a subdomain for your website that will be used exclusively for sending emails. Create an account for your sender and begin using it for your newsletter. This avoids overwhelming their inbox and maintains the health of your sending domain.
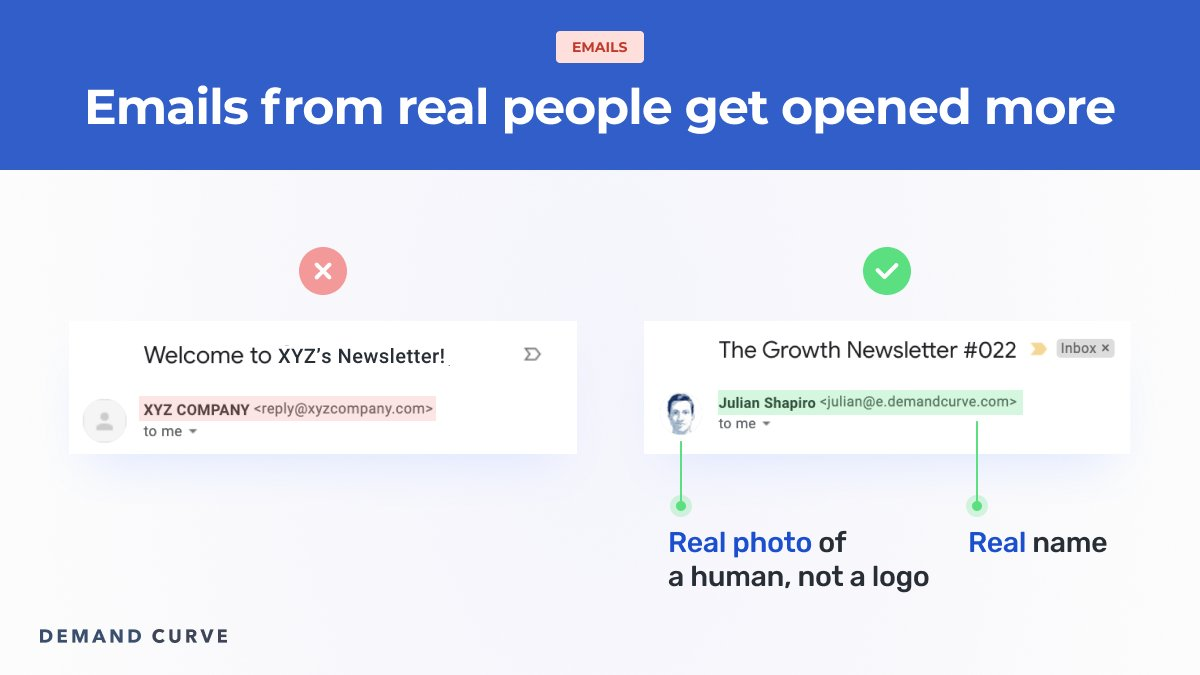
Image Credits: Demand Curve
Send a superissue to new subscribers
A new subscriber will be keen to receive their first issue. To ensure they’re satisfied, piece together your best content from past issues into a superissue. But be careful not to use the same content you included as samples on your sign-up page.
Send this first superissue with the welcome email so that your new subscribers are immediately receiving value from your newsletter. Starting with your best content first will get your subscribers excited to open future emails.
We’ve found that shorter welcome emails perform better than long-winded ones. Keep your welcome message short and your opening issue tight. Once they’ve received the welcome email and the first superissue, add them to the regular email cadence.
Image Credits: Demand Curve
Consider sending fewer emails
We polled over 24,000 marketers on Twitter asking whether people suffer from “newsletter fatigue,” causing them to unsubscribe.
The results: 80% of respondents unsubscribe when they get too many emails.
To avoid overwhelming your subscribers:
Give your subscribers control over how often they are emailed: Some subscribers want them weekly, while others want monthly. In the footer of your email, create opt-out links that allow subscribers to customize the cadence they’ll receive emails. Giving them the opportunity to opt out of frequent emails while still remaining subscribed keeps them as valid contacts on your email list. You want to avoid losing them completely as a subscriber.
Send fewer emails: Putting a constraint on how many emails you’re allowed to send every quarter will force you to be more thoughtful about the contents of those emails. A high volume of emails just for the sake of being in your subscribers’ inbox can burn you and your readers out. We’ve seen very little correlation between volume of emails and the resulting conversion rate.
Make your emails fun — not just educational
Most emails in your inbox are serious. To stand out, consider injecting some lighthearted memes, jokes or interesting links from around the web.
We’ve found this tactic works extremely well, because it gives your readers a dopamine hit in every email. Not every piece of newsletter content you write will resonate with every subscriber. Humor, on the other hand, can have broad appeal. Including interesting and fun content will ensure that every reader is left feeling satisfied.
It also helps build a habit. If every edition is slightly different, your reader will never be sure what they’re opening when a new edition hits their inbox. We’ve found that including something fun at the bottom of the newsletter gives readers a reward: Read the serious stuff, then get rewarded with the fun stuff.
We add a meme to each issue. People reply to tell us how much they appreciate it.

Image Credits: Demand Curve
Make referrals seamless
Referrals are a free way to grow your newsletter. To increase the chances of subscribers referring you to others, make sure the process takes no longer than 25 seconds.
Remind readers at the end of each issue that they can refer others. A simple way is to ask them to forward the email to a friend who would find it interesting. Include a short sentence in the intro to your newsletter telling people being referred where they can subscribe. Include a link.
An advanced tactic is to include a subscriber’s unique link to a referral program so they can track how many people they’ve invited. Give them the option to share through email or social media.
You should also have a web version of every issue so that your content can be easily shared outside of email. Most email service providers will automatically generate a web link that you can promote through social media or elsewhere. You can also copy the content and post it to your website as a blog post to generate traffic from search engines.
Consider providing rewards to those who refer your newsletter. Merchandise will likely only work as an incentive if your brand is well known or very unique. We suggest incentivizing referrals using exclusive content. Send a monthly bonus issue to subscribers who have referred five or more friends. This will keep your costs down and give your subscribers more of what they already want.
Note that you will need a critical mass of subscribers before referrals will prove to be effective. We’ve found the threshold is about 10,000 subscribers. But if your audience is extremely engaged or the community you serve is active, implementing a free referral program has virtually no downside.
How to turn followers into subscribers
Your subscribers will likely become aware of your content through a social media channel, but social media audiences are rented from the platform — you do not own a direct channel to communicate with them. Converting followers into newsletter subscribers is one way to control a direct line of communication and deepen your relationship with your audience.
When pitching your followers to subscribe to your newsletter, include a link in your bio. This may sound obvious, but many people don’t do it. When someone comes across your social media profile, make signing up for your newsletter the call to action. Otherwise, they’ll have no idea that you even have a newsletter.
You could also cut a Twitter thread or LinkedIn post short and tell people to subscribe for the rest of the insights. You probably don’t want to overuse this tactic.
Create an offer or unique piece of content that can only be accessed through the newsletter. This will motivate your followers to join your email list to get access to exclusive content or unique offers.
Recap
Getting new subscribers: Use pop-ups that are relevant and only to high-intent readers on your site. Provide proof of why they should subscribe to your newsletter with sample content. Make your welcome email stand out and front-load the first issue with your best content.
Keeping subscribers: To keep your subscribers wanting more, send fewer emails. Sprinkle in humor and interesting links to turn your newsletter into a habit.
Promoting your newsletter: Use exclusivity and offers to hook your social media followers into subscribing to your newsletter. Ask your subscribers to refer your newsletter to others to grow your subscriber base.




