If you aren’t drowning in email these days, you either don’t have an email account or you are a very young person who marketers haven’t discovered quite yet (they will!).
To push back against the assault, a 10-month-old, Bay Area-based startup called Gated has emerged with an approach to help both overwhelmed email recipients and hopefully benefit society at large. The big idea: to force unknown senders to donate to a nonprofit chosen by the email recipient in order to get into their inbox. Want to tell strangers about your event next month, pitch your company, sell your gizmo? That’s fine, but it’s going to cost you — maybe a lot, depending on who you’re trying to reach.
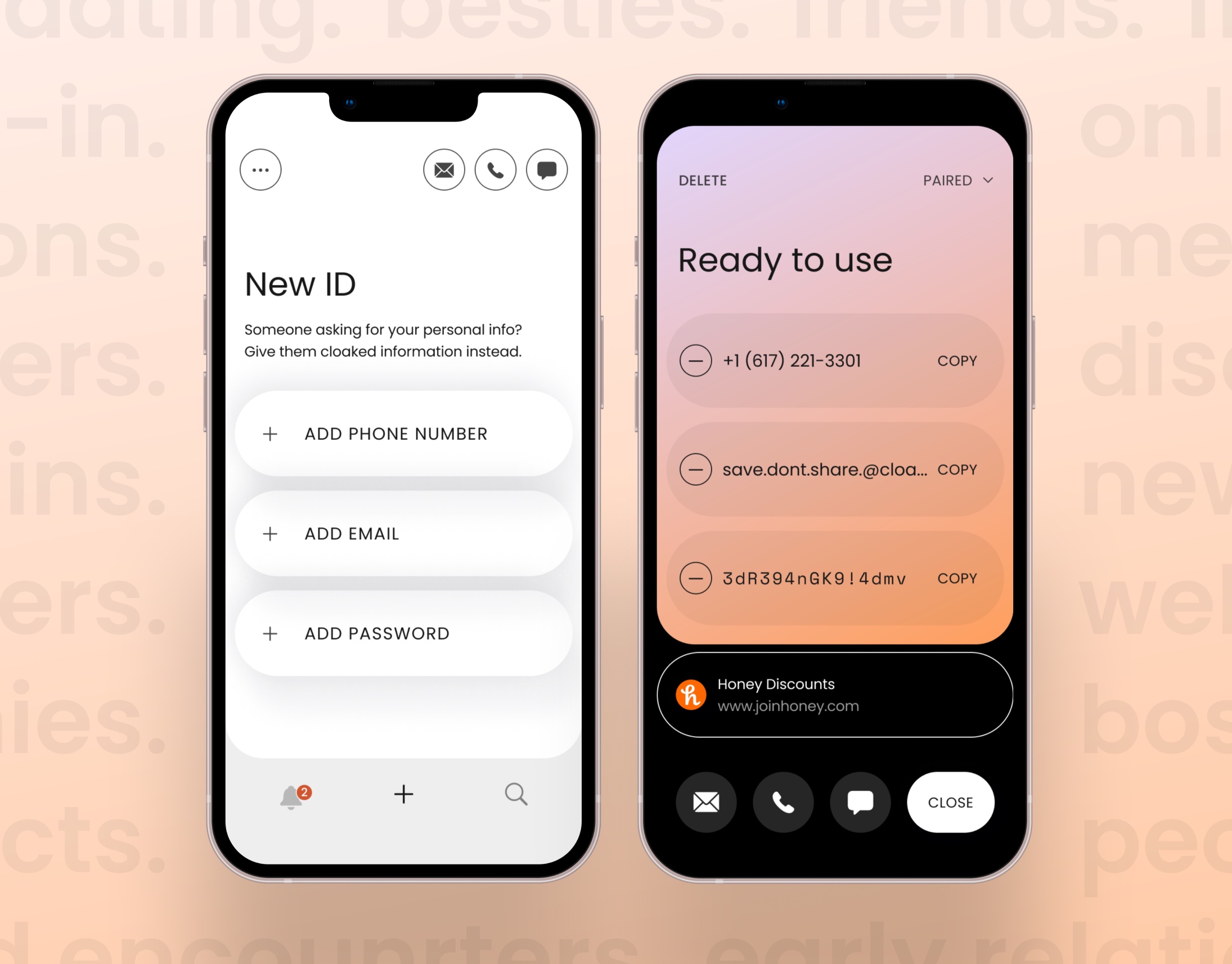
Gated — founded by Andy Mowat, an angel investor who was most recently the VP of growth operations at the employee engagement startup CultureAmp — works by creating a separate folder in one’s Gmail account. According to Mowat, the software automatically builds a list of allowed senders based on who the email holder has communicated with previously; when unknown senders reach out, they’re promptly moved into this separate folder, where they’re told they can only reach the user’s inbox if they make a donation to that person’s charity of choice. The individual sets the price — beginning with a minimum of $2 per email — after which 70% of the payment goes to the (vetted) nonprofit. The rest flows to Gated, whose software is free.
Unsurprisingly, venture capitalists, who are the target of hundreds of pitches each day, love the idea. Indeed, Gated is announcing that it has raised $3.3 million in seed funding led by Corazon Capital, with participation from Precursor Ventures, Burst Capital, Tuesday Capital and other early-stage funds.
Of course, as much as the concept may resonate with potential users (waves hand), it also raises questions, including, first and foremost, around privacy.
For its part, Gated says it never reads the contents of any message. “We’re only looking at the metadata, the ‘to’ and the ‘from,'” says Mowat. Even still, there are only so many people being flooded by enough strangers’ requests that Gmail filters aren’t enough. Some of those people are likely influential in their own way and might not love Gated mapping their connections over time.
Another challenge is that not everyone uses Gmail, which is the only platform to approve the use of Gated’s software to date. (Mowat says the company is going through the “next round of reviews” with Microsoft, noting that some email platforms have “had some other partners burn them in the past” so they “put everyone through a security review.”)
Gated is also not a lucrative business to start, though as with most startups, that could surely change. As Mowat tells us, a large chunk of the revenue Gated expects to receive will end up going toward payment fees to cover the cost of all these transactions. While he and his small team are already thinking about micropayments schemes so Gated isn’t eaten alive by credit card fees, it’s not there yet.
As for how Gated grows, beyond articles like this one, the outfit is counting on a heavy viral component to spread the word at first. That seems like a reasonable approach, given that even two weeks ago, Gated already had a wait list of 2,500 people, according to Mowat, despite having not yet launched publicly.
Later, Gated also plans to develop a business-to-business product, where marketers work with Gated to develop a budget that allows their sales teams to send out a certain number of emails per month.
By the way, if you’re wondering: An email recipient who uses Gated is under no obligation to answer an email, no matter how much someone has paid to get it into their Gmail account.
According to Mowat, the response rate the company is seeing with its beginning user base is higher than average. “Between 40% to 60% of all donated emails are replied to, with some users replying to every single email because they really appreciate people respecting their time.” Others, he adds, still reply “very infrequently.”
It’s also worth noting that a “donor” does not have unfettered access forever to the inbox of an email recipient. “There’s some subtleness to it,” says Mowat, but basically, if a recipient responds to an email, the email sender is placed in a known sender group by default. Still, that sender can be dragged back to that Gated folder at any time.
And there’s a third option called “mute.” Says Mowat, “That basically means, ‘Don’t send them another challenge email. But also don’t put them in my inbox.'”