New SEC cybersecurity disclosure rules: What you need to know to stay in compliance
A year into private ownership, SailPoint cracks the $600M ARR threshold
Enterprise spending on cybersecurity has changed, and vendors must adapt
Even in the usually exciting world of cybersecurity, discussions on enterprise security budgets tend to veer toward the mundane. However, today’s macroenvironment has thwarted almost every market prediction, and while we know for certain that the down market has driven most companies toward austerity, its true impact on cybersecurity spending has remained an enigma — until today.
A recent report by YL Ventures based on data pulled from surveying Fortune 1000 CISOs (chief information security officers) and cybersecurity decision-makers is shedding light on the impact of the down market on buying behavior, how security strategies are evolving in response and how customer interactions with vendors have changed as a result.
The biggest takeaway? Half of CISOs can still accommodate new solutions, and, contrary to low expectations, 45% of cybersecurity budgets remained unchanged or have even been increased. Specifically, a third of respondents (33.3%) report unchanged budgets and 12.2% saw their budgets raised.
Meanwhile, another third (33.3%) of cybersecurity budgets have been cut while 21.2% of cybersecurity leaders are currently managing frozen budgets, meaning that new spending is not possible.
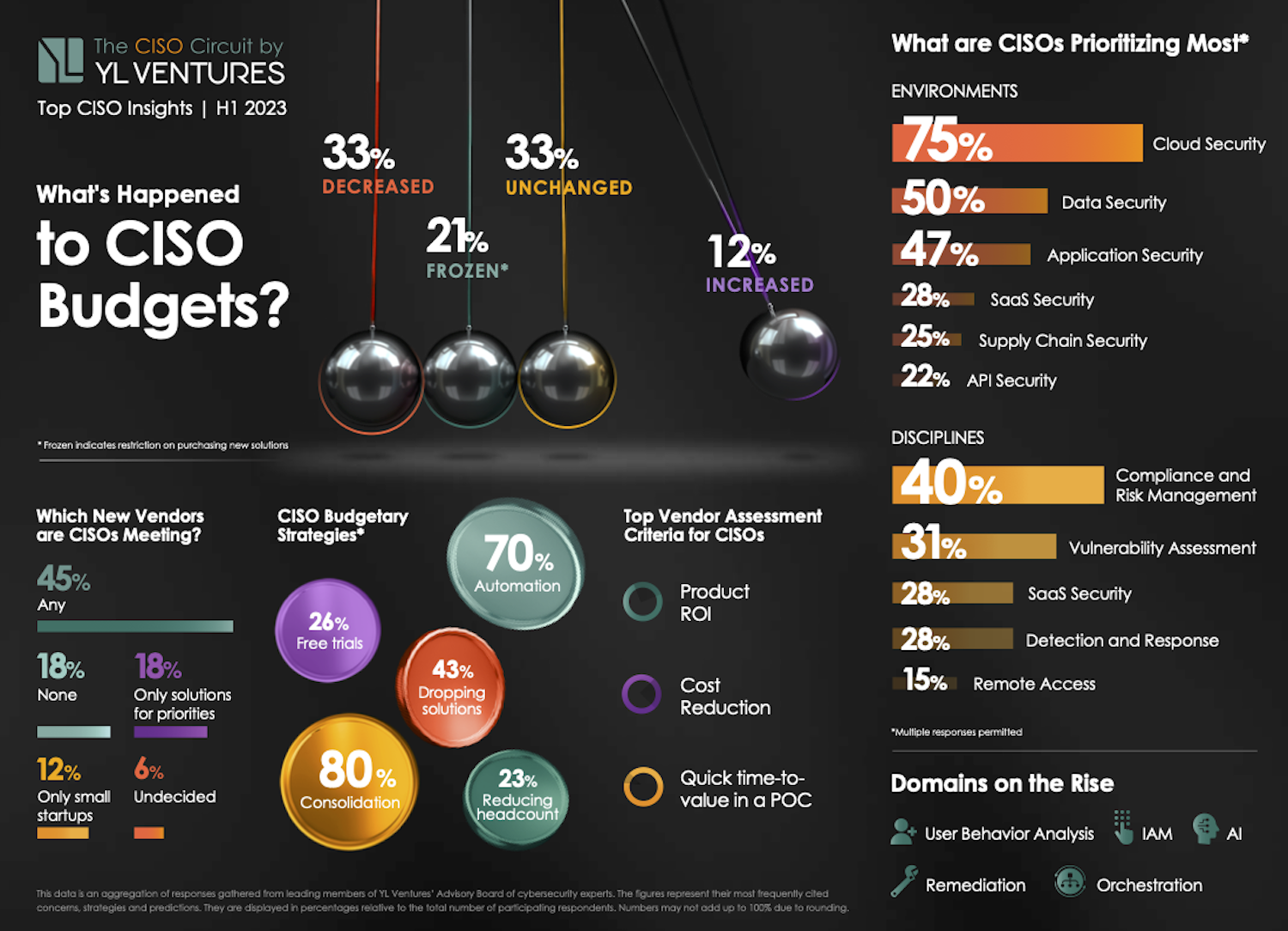
Image Credits: YL Ventures
Making first contact
Though the data may seem intimidating, vendors still have ample opportunity to get a foot in the door. A considerable majority (75.8%) of cybersecurity leaders are still willing to meet new vendors — there are simply more caveats involved. While almost half (45.5%) are willing to meet any vendor, 18.2% are only meeting with those who strictly address their most pressing security priorities and 12.1% are only interested in meeting younger and smaller startups.
Indeed, this is an excellent time for small startups to shine and perhaps for larger vendors to take note. In the eyes of most cybersecurity leaders, smaller and earlier-stage companies tend to offer more advantageous licensing costs as well as design partnerships, which enable bespoke solutions that better suit their unique pain points and operational needs.
Currently, 26.7% of respondents are relying on free trials as provisional measures. If we think back on the more difficult days of the pandemic, when many cybersecurity providers offered their services for free, we can see ample evidence of just how much goodwill such gestures built and how they propelled companies to the top. For vendors who find this too difficult to stomach, consider how effective land and expansion tactics have tended to work in the past, and remember that the rising tide of fiscal conservatism leaves little room for obstinacy.
The MOVEit mass hacks hold a valuable lesson for the software industry
The MOVEit mass hacks will likely go down in history as one of the largest and most successful cyberattacks of all time.
By exploiting a vulnerability in Progress Software’s MOVEit managed file transfer service, used by thousands of organizations to securely transfer large amounts of often-sensitive files, hackers were able to inject SQL commands and access customers’ sensitive data. The attack exploited a zero-day vulnerability, which meant Progress was unaware of the flaw and did not have time to patch it in time, leaving its customers largely defenseless.
Russia-linked Clop ransomware group, which claimed responsibility for the hacks, has been publicly listing alleged victims since June 14. This growing list includes banks, hospitals, hotels, energy giants and more, and is part of an attempt to pressure victims into paying a ransom demand to stop their data from spilling online. In a post this week, Clop said it would leak on August 15 the “secrets and data” of all MOVEit victims that refused to negotiate.
This wasn’t Clop’s first mass hack, either; the group has been blamed for similar hacks targeting Fortra and Acellion’s file-transfer tools.
According to Emsisoft’s latest statistics, the MOVEit hack has affected at least 620 known corporates and more than 40 million individuals. Those figures have increased almost daily since the hacks began.
But how high could the numbers go? “It’s impossible to assess at this point,” Brett Callow, a ransomware expert and threat analyst at Emsisoft, told TechCrunch+. “We don’t yet know how many organizations were impacted or what data was compromised.”
Callow pointed out that around a third of the known victims were impacted via third parties, and others were compromised via subcontractors, contractors or vendors. “This complexity means it’s highly likely that some organizations that have been impacted don’t yet know they’ve been impacted,” he said.
While the impact of this hack is unusual because of its scale, the attack isn’t new in terms of its approach. Adversaries have long exploited zero-day flaws, and supply chain attacks have grown prevalent in recent years because one exploit can potentially affect hundreds, if not thousands, of customers.
This means that organizations need to act now to ensure they don’t fall victim to the next mass hack.
Picking up the pieces
For victims of the hacks, it may seem like the damage has already been done and recovery is impossible. But while recovering from an incident like this can take months or years, affected organizations need to act fast to understand not only what types of data were compromised, but also their potential violations of compliance standards or data privacy laws.
Strengthening security in a multi-SaaS cloud environment
Managing security across multiple SaaS cloud deployments is becoming more challenging as the number of zero-day and ransomware attacks continues to rise. In fact, recent research reveals that a staggering 76% of organizations fell victim to a ransomware attack in the past year.
It’s no secret that protecting data is hard, and with the rise of cloud technologies, it’s becoming harder. But when it comes to cloud SaaS application risk, what does that look like? And what actionable steps can teams and IT pros take to help mitigate those risks at their organization? In this article, I’m going to explore those questions and provide some insights.
Navigating the maze of SaaS challenges
Modern organizations encounter a variety of SaaS challenges, including the absence of configuration standards, multiple APIs, and user interfaces (UIs) with varying access levels and potential data leaks across interconnected systems. Securing structured data in CRM applications, communication data in messaging platforms, and unstructured data from file providers is already difficult.
However, when these systems are sourced from different vendors, it becomes even more challenging to detect and prevent attacks in a timely manner. The interconnected nature of these systems makes tracking data provenance difficult and facilitates broad spread of malware and ransomware.
This challenge is further exacerbated when organizations extend their systems to include external users. With expanding footprints, the inadvertent leakage or destruction of sensitive data becomes a significant concern. Popular platforms like Salesforce Communities, Slack Connect, Microsoft Teams, Microsoft 365, and Google Drive create a complex web of identity, permissions, and integration controls.
Unfortunately, most endpoint management tools on the market were designed for a pre-cloud, pre-bring-your-own-device (BYOD) era, making them inadequate for managing the modern SaaS landscape. So how do you take control?
Taking control with new solutions
When managing risk in the cloud, it’s crucial to select IT and security solutions that truly address the intricacies of the deployed SaaS applications and were born 100% in the cloud without any legacy on-premises components. The good news is that vendors are developing innovative solutions to help IT and security teams do this. But it’s essential to explore the options and consider the following:
First, do they go beyond basic factors such as OAuth scopes, login IP addresses, and high-level scores, and instead delve deeper into data usage patterns and even examine the code of all integrations?
Second, many major SaaS vendors provide event monitoring, antivirus protection, and basic data leak prevention as check boxes. But these features often fall short when it comes to preventing and remediating data attacks because of miscalibrated thresholds in alert systems and logs that are not tuned for specific organizations. That results in alert overload and fatigue. It’s important to understand how a solution improves risk scoring and alert prioritization.
Cyber insurance audit: Painful necessity, or a valuable opportunity?
Not that long ago, few companies even considered purchasing insurance to mitigate their financial exposure from a cyber incident, and for those that did, obtaining a policy was as easy as filling out an application and writing a check. Those days are now squarely in the rearview mirror. Today, companies everywhere are rushing to get cyber insurance — the value of the global cyber insurance market reached $13.33 billion in 2022 and is projected to soar to $84.62 billion by 2030.
However, the increased number of policies combined with the sharp uptick in costly attacks led to higher costs for cybersecurity insurance providers. To stem their losses, insurance companies now often require proof that an organization has implemented a variety of security measures in order to be eligible to purchase a policy.
Rather than resisting or resenting risk assessments from potential cyber insurance vendors, IT leaders should regard them as an opportunity to strengthen their organization’s security posture.
Cyber insurance involves risk assessment
Across the insurance industry, policy requirements and premiums vary according to risk assessment. For instance, installing an anti-theft system might reduce the cost of insuring an expensive sports car. A person living in a flood plain can expect to pay more for a homeowner’s policy than someone with a similar house on higher ground — or they might not be able to purchase a policy at all, as homeowners in states like Florida are discovering.
It is the same for cyber insurance. An insurance provider may impose more security demands on a company that hosts large volumes of personally identifiable information (PII) than it does for a company of similar size with far less PII. And organizations that lack sufficient security controls to bring risk down to a level acceptable to an insurance provider might not be eligible for any policy at any price.
What cyber insurance actually covers
The main focus of cyber insurance is obviously on covering the financial risks of an incident. Typically, you can expect the insurance to cover the firsthand costs to the business that are the direct result of the cyber event, such as:
- Forensic analysis and incident response. Some insurers require that you engage specific managed incident response services.
- Recovery of data and systems caused by actual loss and destruction.
- Cost of the downtime due to the cyber event.
- Costs incurred from sensitive data breaches, such as handling PR activities, notifying impacted clients, or even providing credit monitoring services to customers.
- Legal services and certain types of liability for regulated data, including covering the costs of the civil lawsuits.
It is important to note that insurance rarely or never covers some of the longer-lasting impacts of the event, such as any future profit loss due to theft of intellectual property or the need to invest in cybersecurity program improvements after the event.
There is no consensus on reimbursement for paying a ransom. Not all insurers cover this type of expense. Some experts argue that it can encourage further attacks and fund criminal activities. In some jurisdictions, the discussion is going back and forth on whether paying ransom should be banned altogether.
As with any insurance policy, you can expect extra clauses. These may include the top amount they cover, the requirement to go through a due process with the law enforcement agencies, or involvement in professional ransom-negotiation services.
The must-have security measures for cyber insurance
A recent Netwrix study reveals useful details about the process of qualifying for cyber insurance today. It found that 50% of organizations with cyber insurance implemented additional security measures either to meet the requirements of the policy they selected or to simply be eligible for a policy at all. The figure below shows the specific requirements they reported having to meet:
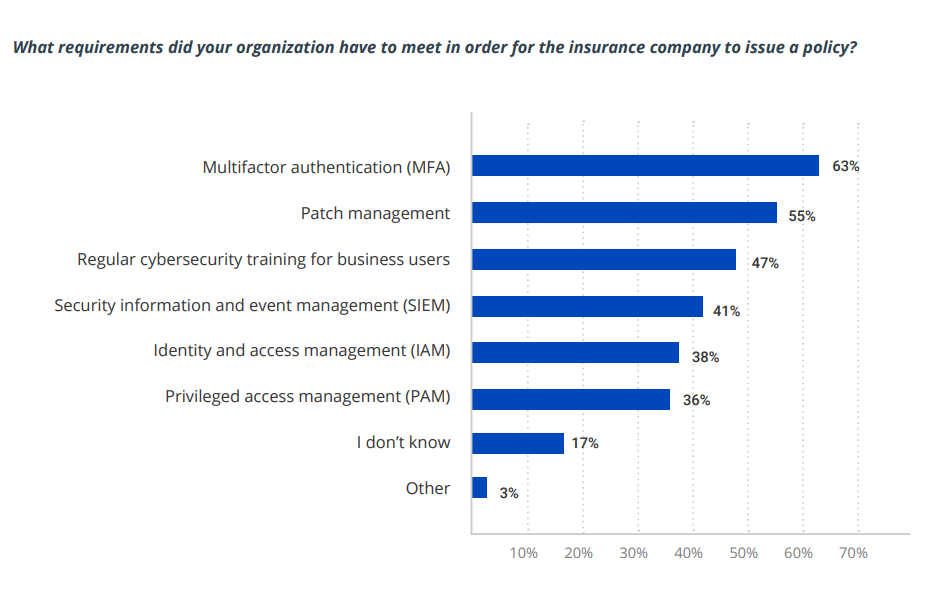
Image Credits: Netwrix/Netwrix Hybrid Trends Security Report 2023
Don’t take this list as comprehensive or authoritative. For instance, implementing MFA does not necessarily mean requiring MFA for all users; an insurer might require additional authentication only for users with privileged access to sensitive data and systems. In addition, remember that these controls are interrelated. For example, in order to require MFA for access to particular types of data, you need to know where sensitive and regulated data resides and have control over user and administrative privileges.
Wormhole digs out of its hole with new security measures to move on from $320M hack
Many projects and companies would simply give up if they’d been hacked and had hundreds of millions stolen from their ecosystem partners, but it appears Wormhole isn’t one of them.
Last year, an attacker exploited a vulnerability in the Wormhole liquidity bridge between the Ethereum and Solana blockchains and stole about 120,000 wrapped ether, worth about $223 million today. A bridge, like the name suggests, facilitates transactions between different chains.
Shortly after the hack, Jump Crypto tweeted it was replacing the massive chunk of ether stolen to “make community members whole” because it saw Wormhole as “essential infrastructure” for the future’s multi-chain world.
Almost a year-and-a-half later, the cross-chain crypto bridging and messaging protocol seems intent on learning from its mistakes and making a comeback.
Since the hack, the company has stepped up its security, launched two $2.5 million bug bounty programs, and had a handful of third-party firms do a number of audits to resolve critical issues. The company has paid out several bounties, and by the end of the year, plans to add three core contributing teams that will be “building in various capacities,” Dan Reecer, head of operations at Wormhole Foundation, told TechCrunch+.
The company has finalized four teams so far and will potentially add one more, Reecer added. These teams will focus on building messaging protocols, zero-knowledge technology, business development, front end tools, blockchain tools and more. “It’s skill-dependent and we’re bringing teams that have [these different] components,” he said.
Wormhole also became one of two bridging protocols chosen by the Uniswap DAO for its cross-chain messaging after a study found the bridge fulfilled the necessary security requirements, according to Uniswap’s Bridge Assessment report.
The approval stems from the number of validators, including “reputable entities,” as well as “significant improvements” in response to its exploit in February 2022, the report added. However, the report identified some areas for improvement and “recommends periodic monitoring for any material changes that may affect the protocol’s security profile.”
Summing all that up: While Wormhole has indeed stepped up and improved its security around the protocol, there are still risks and concerns for its validators in the way the protocol bridges transfer messages and tokens.
But why did it take an exploit for Wormhole to ramp up its security efforts?
Reecer said he couldn’t comment on why Wormhole didn’t implement these measures before, as he joined the team only a few months ago, but he did note that security is always going to be one of the biggest priorities for the company.
“Maybe people didn’t realize at the time [of the hack] how important this was,” he added.
Big efforts, small potatoes
8 VCs explain why there’s good reason to be optimistic about cybersecurity
It wasn’t long ago when it seemed like the tide was beginning to turn on ransomware. But 2023 has shown us that’s not the case: We’re only half way through the year, yet hackers are already claiming more victims than ever before, reaffirming the importance of cybersecurity for every business.
While 2023 has been fruitful for hackers, it has been less so for the startups trying to defend against them. Investment in cybersecurity has fallen well below the record highs recorded in previous years: security startups saw $2.7 billion in funding the first quarter of the year, a 58% drop from the $6.5 billion recorded in Q1 2022. And just 149 were deals announced in Q1 2023, the lowest total in years and a 45% drop from a year earlier.
We’re looking for founders to participate in a TechCrunch+ survey about the usefulness of various founder-focused events.
If you’re a founder and have something to share about your experiences at such events, fill out this form.
Investors, however, remain optimistic. The explosion of large language models and generative AI has many excited about the technology’s potential in the cybersecurity space. Others believe that the need to secure the cloud and connected devices — coupled with a drop in valuations — makes now the perfect time to invest.
We checked in with some of the leading investors in cybersecurity to hear their thoughts on the funding slowdown, what market trends they are most excited about, and cybersecurity’s ongoing diversity problem.
We spoke with:
- Alex Doll, founder and managing general partner, Ten Eleven Ventures
- Barak Schoster, venture partner, Battery Ventures
- Sheila Gulati, managing director, Tola Capital
- Umesh Padval, venture partner, Thomvest Ventures
- Andreas Calabrese, general partner, Tampa Bay Ventures
- Deepak Jeevankumar, managing director, Dell Technologies Capital
- Mark Kraynak, founding partner, Acrew Capital
- Ariel Tseitlin, partner, Scale Venture Partners
Alex Doll, founder and managing general partner, Ten Eleven Ventures
Funding for cybersecurity startups has flatlined. How has your investment strategy changed to reflect the new market conditions?
We successfully closed our latest cyber-only, stage-agnostic global fund in June 2022 and are actively deploying capital from it. Despite the current environment, our investment strategy is largely the same as it has always been, although, within our cyber-only, stage-agnostic and global mandate, we are always agile and adjusting to look for the stages, sub-sectors and geographies where we see the most significant opportunity at the best value.
Right now, those sub-sectors include new approaches in the software supply chain, identity, privacy and trust. We are actively investing across stages where we see market opportunity and compelling tech. Just last week, we announced a seed investment in Silent Push and a Series B investment in Blackbird.ai. We’re still hunting actively, including meeting with several inspiring entrepreneurs at InfoSec in London.
While growth-stage opportunities have decreased at the pre-IPO stage with the downturn in the public market, we’ve found some very exciting prospects at Series B and C, where non-cyber specialist funds have pulled back, and we’ve been able to be strategic in helping those companies on their next chapter.
What advice would you give your portfolios to survive the current challenging market?
During uncertain and potentially scary times like these, leaders must stay close to their teams, communicate an inspired and motivating vision, and give team members time together to solve problems collaboratively. This kind of culture can be challenging to reinforce as we normalize from the pandemic; we are still adjusting to remote work routines, and have experienced a lot of shocks (including the SVB crisis) over the last 12 months. But it is more important than ever.
Given that many public cybersecurity companies are posting faster revenue growth than other tech companies, should cybersecurity startups lean more heavily into pursuing revenue growth over cash conservation than the average startup today?
There has undoubtedly been a shift in perspective; investors are now more heavily weighting capital efficiency metrics when making investment decisions for cybersecurity companies raising new rounds. So companies need to keep these metrics in mind, especially early on, and as they approach maturity.
On the other hand, companies should be mindful of not “starving growth” by underinvesting in sales and marketing or, importantly, R&D. Experimentation is still essential when developing the best go-to-market strategy for new products and for new audiences.
There should be more intention around measuring the spending on R&D and looking for leading indicators of success as projects develop. For example, there is always a lot of attention on quantifying the marketing/sales funnels and channels (and for good reason), but I am always amazed at how little time is spent on R&D productivity metrics. R&D productivity stats may be less developed and more subjective to a degree, but that’s “art” that is required learning for every cybersecurity CEO.
Every R&D resource needs to be accountable to the team/business, like sales and marketing are accountable every quarter. For example, measuring innovation release cycles and the number of true “market tests” can be a very predictive but overlooked statistic for early-stage companies. Great companies have an inherent urgency in their innovation cycle times.
Is cybersecurity-focused venture capital in a downturn? Do you expect venture investment in the category to pick up in the back half of the year?
While there has been a decline, cybersecurity investing will accelerate again within the next 12 to 18 months. Cybersecurity spending is still a priority for enterprises, and we are seeing interesting new investment areas — including protecting AI and organizations from the risks of disinformation — that will propel more investment rounds going forward.
Additionally, new funds are being raised right now in the space that will contribute to increased funding levels in the future. Overall, cybersecurity is still seen as a strong growth area, and it is resilient compared to many other sectors.
Valuations have dropped, yet cybersecurity M&A activity remains flat. Are you accelerating your cybersecurity investments to take advantage of lower prices?
We are active where we see well-priced opportunities, of course, and it is refreshing to invest when expectations on valuation are not so inflated. So, yes, we believe it is a good time to invest, and we are actively looking for companies with expectations aligned with today’s environment.
Recent data shows that only 24% of the cybersecurity workforce are women. Are you seeing changes in cybersecurity founder demographics, or do they mirror what we’re seeing amongst cyber workers more generally?
While most cybersecurity founders we meet are men, we’re seeing increasing numbers of women executives in these companies. Notable examples of innovative CEOs in our portfolio are Poppy Gustafsson, CEO of Darktrace, and Anusha Iyer, founder and CEO of Corsha.
A lot of the research and thought leadership within the portfolio is coming from women, such as Marta Janus, principal adversarial ML researcher at HiddenLayer, or Amanda Berlin, lead incident detection engineer at Blumira, which is exciting. We are actively meeting with new female founders and executives all the time, and would love to meet others who are looking to speak with a cybersecurity specialist investor.
Looking ahead, what cybersecurity trends are you most excited about from an investing point of view?
We think that AI brings several new dimensions to the cybersecurity sector, including augmenting security analysts and making traditional security operations tools easier to use. Also, as you can see with our recent investment in HiddenLayer, machine learning models, including LLMs, must be protected from malicious attacks. We also closely watch new risks emerging from AI-enabled automation, including bots, and symptoms like vast amounts of quickly spreading disinformation.
How do you prefer to receive pitches? What’s the most important thing a founder should know before they get on a call with you?
Historically, we have invited founders to submit via our website or email. The most important details to include are the team’s background, product idea, initial thoughts on early/milestone customers, and some idea of a round size, as well as some thoughts around the “use of proceeds”: Why that amount is required and how the founder would spend it in the next 18 to 24 months to get to the next milestone.
Before they get on a call with us, founders should know that we are cybersecurity specialist investors and already have a lot of knowledge on general dynamics in the space. So beyond general statistics on breaches and industry growth, we would like to know the founder’s unique experience in cybersecurity and how that contributes to the product they are looking to build and grow.
We would like to see early evidence that they are getting early and rapid feedback from potential buyers or design partners. The founding team’s ability to receive and iterate quickly on this feedback is very important. Great companies have inherent urgency in their innovation cycle times, and we think this predisposition can be seen very early in the DNA of a winning founding team.
Barak Schoster, venture partner, Battery Ventures
Funding for cybersecurity startups has flatlined. How has your investment strategy changed to reflect the new market conditions?
Our investment strategy remains consistent. I founded a cybersecurity company before becoming a venture capital investor, and my passion for the sector has not changed. Cybersecurity remains a critical area of focus for Battery, and we have expanded our scope to include other related sectors, including privacy protection, developer tools, cloud computing, data analytics and artificial intelligence. We aim to capture opportunities in adjacent markets that have synergies with the cybersecurity market.
We maintain a long-term perspective and prioritize investments in startups with promising technologies and strong market potential, even if the immediate funding landscape is challenging.
What advice would you give your portfolios to survive the current challenging market?
Focus on the customer: Continue building software that people want, meet customer needs, listen to feedback and proactively address their pain points. Additionally, many cybersecurity companies may need to revisit their go-to-market strategy by exploring different distribution methods (such as direct, managed security service providers, value-added resellers, open-source, self-service, etc.); by adapting to the needs and compliance regulations of customers in newly emerging market segments; and by investing in research and development to uncover new opportunities, improve efficiency and differentiate themselves in the market.
It is also critical that companies preserve cash flow and ensure efficient resource allocation. We are advising our companies to closely monitor cash flow and maintain a healthy financial position to ensure sustainability.
8 VCs explain why there’s good reason to be optimistic about cybersecurity by Carly Page originally published on TechCrunch
Crypto losses halved in Q2 2023 to $204M
As if the pessimism around crypto wasn’t enough, the industry has historically been hounded by hackers and scammers looking to make a quick buck. To make things worse, it appears tracing and recovering lost funds is now getting harder than ever as attackers use increasingly sophisticated methods.
According to a new report, only $4.9 million was recovered of the $204.3 million the industry lost to hacks, scams and rug pulls in Q2 2023, and that was significantly less than the $6.9 million recovered in Q2 2022. However, the good news is that losses in the second quarter were 55% narrower than in Q1 2023, when the industry lost a whopping $462.3 million to hacks and scams, with the Euler Finance flash loan attack accounting for 42.4% of the first quarter’s losses, REKT’s database showed.
The report, by web3 “super app” and antivirus solution De.Fi with supporting data from the REKT database, detailed that so far this year, the industry had recovered about $183 million, or nearly 28% of the $666.5 million lost to scams and hacks.
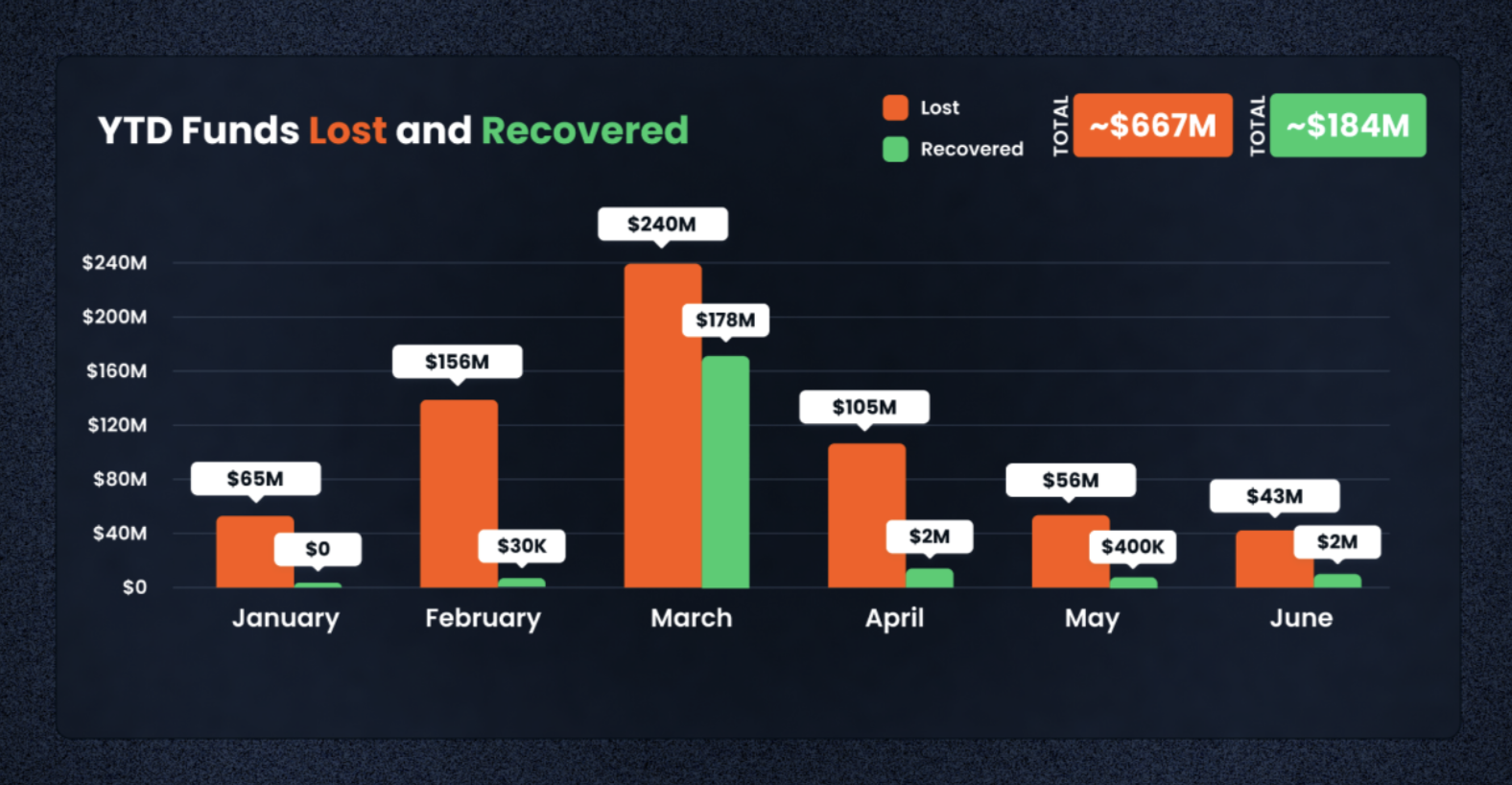
Image Credits: De.Fi, REKT
Q2 saw over 100 exploits
This quarter had 110 recorded cases of “scams, exploits or unintended losses,” the report stated. The three biggest cases were the Atomic Wallet breach at $35 million, Fintoch at $31.6 million for its alleged Ponzi scheme, and the exploit of a vulnerability in MEV Boost’s software that led it to lose $26.1 million. These three accounted for a combined $92.8 million, almost half of the total losses in the quarter.
Crypto losses halved in Q2 2023 to $204M by Jacquelyn Melinek originally published on TechCrunch
